Dedicated private linesDedicated private lines work like the toy phone children make by connecting two tin cans with a string. The tin can phone can only be used to communicate between two points across the string, such as between two tree houses. Like the string, dedicated private lines connect two separate points. For this reason, dedicated private lines are often called point-to-point circuits. Other names are dedicated circuits and leased lines. A state university, for example, may use dedicated private lines to share data between the main campus and its various satellite campuses.
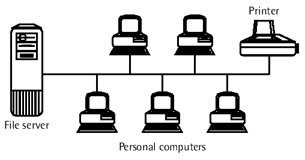
The original data networks consisted of dumb terminals connected to a mainframe computer across dedicated private lines (see Figure 1). Data processing required a giant mainframe computer. It was more cost effective to have one mainframe computer at a central location than to have a computer at each remote site. The word “dedicated” means the phone company reserves the phone line from point A to point B just for you. The line is called private because no one else can use it.
 Figure 1: The original data network consisted of dumb terminals at remote sites connected to the mainframe computer at the home office.
Figure 1: The original data network consisted of dumb terminals at remote sites connected to the mainframe computer at the home office. The monthly cost of a dedicated private line is based on distance and bandwidth. The longer the distance, the greater the cost. The greater the bandwidth, the greater the cost. The bandwidth of most dedicated private lines is 56 Kbps, 256 Kbps, or 1.544 Mbps. Dedicated lines are expensive because the customer ties up the carrier’s line all the time, preventing that line from being used by other customers.
The telephone companies appreciated the revenue from sales of dedicated private line service, but they feared that their networks would run out of room. As data networking began to be used by more and more businesses, the telephone companies could see that one day they would not have enough lines to meet demand. They had two choices: build more phone lines or figure out how to get more data across existing lines. They chose to do both. Engineers went back to the drawing board and came up with a brilliant solution: circuit switching.
Even though circuit switching (and eventually packet switching) is a more recent technology, dedicated private lines are still used in most data networks. Depending on the application, dedicated private lines require the use of the following types of data communication equipment: modem, channel service unit, data service unit, channel bank, or a PBX. A networking specialist normally helps a business decide what equipment is needed in a given application.
To lease or buy?Data networks require the use of customer premise equipment (CPE). Some examples of data networking CPE are modems, channel service units, data service units, channel banks, network adapters, routers, and switches. Some businesses choose to purchase the equipment at the time of installation, while other companies prefer to lease, or rent, the equipment. The lease payment is normally included as a line item on the carrier’s monthly bill.
Once a data network is up and running, most businesses do not give much attention to the invoices. Consequently, a business may end up leasing or renting a piece of equipment indefinitely. The business may be able to save money by purchasing the equipment outright, rather than making monthly payments.
The local loopIf the two endpoints of a dedicated private line are in the LATA, then the LEC will provide the service. For example, a hospital in Salt Lake City, Utah, has a 56-Kbps dedicated private line to a pediatrician’s office across town (see Figure 2). Because the private line starts and ends within the same LATA, U S West provides the service. The same hospital may also have a 56-Kbps dedicated private line to a laboratory in Las Vegas, Nevada. Because this private line crosses LATA boundaries, an IXC, such as Sprint, provides the service.
 Figure 2: Local loops.
Figure 2: Local loops. This interlata private line consists of three parts: the local loop in Salt Lake City, the interexchange mileage, and the local loop in Las Vegas. The local loop in Salt Lake City is the connection from the customer’s premise to Sprint’s nearest central office in the same city. The IXC mileage is the middle portion of the line and runs between Sprint’s central office in Salt Lake City and its central office in Las Vegas. At the other end of the line, in Las Vegas, the local loop is the connection from Sprint’s central office to the customer’s premise.
The two local loops are actually services provided by the LEC in each city, but all three charges will appear on one bill from Sprint. Sprint will procure these services for the customer from the LEC. Sprint will bill the customer for all three portions of the circuit. For the two local loops, Sprint will pay wholesale prices to U S West and Nevada Bell.
Local loop pricing is based on bandwidth and the distance to the central office. The further out the business is, the greater the cost. The bill for the middle portion of the private line is based on mileage and bandwidth. A good rule of thumb is that dedicated private lines generally cost $1 for every 1 or 2 miles. The following sections offer some basic strategies for saving money on dedicated private lines.
Check for missing discounts and promotionsWhen negotiating contracts for data services, telephone companies send out their best field sales representatives. Managers often get involved to ensure that the deal is closed. After the contracts are inked, the highly-polished, high-powered account team turns the service orders over to a data entry clerk, who is probably required to enter orders and answer customer service calls at the same time. The new service is installed, and the new account will be established with no glitches, but the special discounts and promotions frequently “fall off” the account. The end result is that the customer ends up paying the nondiscounted tariff list price for the service.
Most large businesses manage their telecommunications centrally. For example, a large Midwestern printing company with many offices around the country had complex data services with MCI. The telecom department at the corporate office negotiated specific discounts for MCI’s data services. The pricing structure was complex and offered different discount percentages on different services. For example, access T-1s received a 10% discount, frame relay permanent virtual circuits (PVC) received a 15% discount, and interstate dedicated private lines received a 20% discount.
After the contracts were signed, it took MCI many months before the discounts appeared on the bills. Some locations never saw any discounts, or the discounts were applied at incorrect percentages. Access T-1s that should have had a 10% discount instead received only 5%. On some services, the discounts fluctuated each month. The bills for the Tampa, Florida, office may have been accurate in July, but in August, the discounts had vanished. In September, the discounts were back, but at incorrect percentages.
The situation continued for many months. Every month, the corporate telecom department spent days auditing the bills and weeks negotiating invoice credits with MCI. The root of the problem was never pinpointed but it probably had something to do with having such a large, multilocational account processed by a “legacy” billing system. Antiquated billing computers (called “legacy” because they are so old) are still used by most of the large carriers, because they are hard to replace when they are in use every month.
After a few billing cycles, the MCI account team was very discouraged by its inability to correct the problem, and the company was only responsive when the customer hinted at changing to another carrier.
Customers should scrutinize their bills for the first few months to ensure that all discounts are in place. If discounts and promotions are missing, the carrier should correct the errors and issue a refund of past overcharges. If the situation continues, the customer may be justified in switching carriers. Customers must carefully review their carrier service agreement to see if they are justified in canceling the contract and moving to another carrier.